Hosting with High Availability and Ceph File Storage - Why Order
Business transition to online is inevitable. But along with the increase in sales of goods and services, there are risks associated with reputation management. If the site is not available for more than 10 minutes, then not only the company's reputation suffers. Search engines can lower their positions, again they will have to invest in development and promotion. And in the case of hacker attacks - also to restore the site.
The second risk is DDoS attacks. DDoS attacks are organized by hackers on their own initiative or at the request of competitors. A powerful attack leads to server crashes. During this time, you are not accessing the datastore, and clients are not accessing the site.
Why Ceph
What to do? Not going online? No, this is not an option, because as Bill Gates said: "If you are not on the Internet, then you do not exist".
How to publish a project on the Internet?
There are several options: standard classic hosting, shared hosting, dedicated server. Everyone uses these hosting services, they are available. However, they are available not only to you, but also to hacker groups.
In the event of a hosting failure due to DDoS attacks, recovery is slow, and time is your money. The server part is administered manually, which does not exclude the human factor and errors.
But most importantly, your project is stored in one dedicated space, which means it has a point of failure.
We recommend basing your data on our servers built on the Ceph architecture. You can order a reliable storage of your data (website, data, service) in this form.
If you want to learn more about the technology, read on.
What is CERN

The file storage system has a block system. It is fully customizable and easy to administer. The file system is compatible with various programming languages, provides the fastest access to stored objects.
The Ceph file system is designed for maximum performance. Today, losing time is tantamount to losing business, and your image and your business depend on the speed of website loading.
The main advantages of CERN
- Has a fault-tolerant file structure.
- Scalable to any size, and therefore, you can store any amount of information on servers.
- Has no points of failure and bottlenecks.
- Has a high data transfer rate.
- Provides load balancing across clusters.
- Completely free and supported by developers.
Ceph is a fail-safe hosting technology that makes your website always available. You will not lose data even if there are failures in case of emergency.
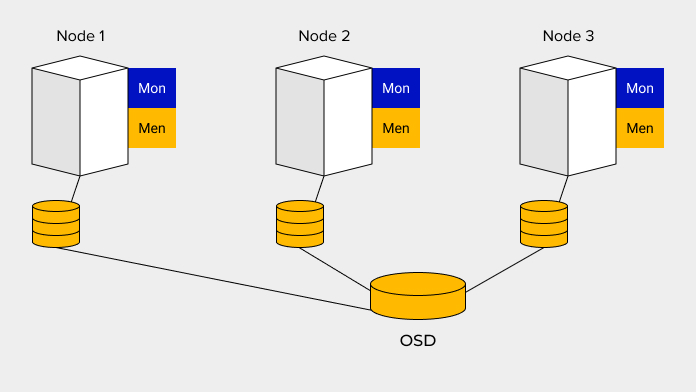
If one of the disks fails, the data is not lost, and the site does not stop working. All your project data have copies saved on the server. Actions with servers are transparent and easy to monitor.
How many copies of the project are stored in Ceph
It depends on a variable that changes on the fly: size. Depending on what value you assign to it, so many copies will settle on the servers. For example, size = 3 - three copies of the project, size = 4 - four copies of the project, and so on. Moreover, the software itself redistributes and copies data; this does not require human intervention. This eliminates the human factor and associated errors.
Pool and data
The system stores all data in pools - a container that can be stored on one disk or on several. Each of the containers (pools) has its own point of failure and replication (size), as well as the storage location, data center, disk, etc.
Ensuring Reliability: CRUSH Algorithm and Caching
Pathmaps are no longer stored on servers, which reduces search overhead. Thanks to the CRUSH algorithm, the load on the servers is reduced. The object path is requested through the monitor, and each client requests it independently. In addition, initially the map is flat, but if you want to distribute information across different servers, you can easily do this and turn the plane into a tree.
Caching
This method assumes that information is first written to the OSD, then clustered, and only logs remain on the disk itself. The method is simple, robust, but not scalable. If you need to make quick changes, it is better to use cache tiering.
SSD Journals
This method assumes that information is first written to the OSD, then clustered, and only logs remain on the disk itself. The method is simple, robust, but not scalable. If you need to make quick changes, it is better to use cache tiering.
Cash-tearing is flexible and easily scalable. With frequent requests and high load, the client enters the hot pool of the SSD disk. As soon as the load is reduced, the object moves to the cold area of the HDD. In cache tiering, you can replace the SSD quickly, and all temperature and time parameters are adjustable.
What it gives you as a customer
If you are not a programmer and do not plan to install your software, deal with pools, monitor monitors, and so on, you simply get: a server, differentiation of access rights, a gateway and the ability to perform calculations.
Using Ceph allows you not to think about hardware and servers - Ceph distributes everything itself, checks server responses, regulates the distribution and operation of projects. You can use Ceph as a data store.
Why Ceph by dZENcode ?
- We use fault-tolerant servers and high availability technology to minimize downtime in the event of hardware failure. The server works 24/7. We guarantee high speed, availability and continuous operation of servers, which is extremely important for your project.
- You do not have to administer your servers, since this task lies entirely with us. We have located the company's servers in countries where they are most secure.
- We use a high-speed connection for work.
- The system has no points of failure, so access to your project, even a highly loaded one, will be uninterrupted.
If you still have questions or doubts, we will tell you about the advantages and disadvantages of each of the storage systems (hosting) in simple language. Get highly resilient servers now without forcing customers to look for you on the internet.
